Cyber Security
October 2025 is Cyber Security Awareness Month
October is Cyber Security Awareness Month (Cyber Month) in Canada and we at the University are proud to be a Get Cyber Safe champion working to help Canadians stay safe online. Cyber Month is an important time to reflect, as individuals and as an organization, on how we can protect ourselves and our loved ones online.
What does it mean to be a Cyber Month champion? It means that the University of Winnipeg will be engaging with Get Cyber Safe’s online campaign and sharing expertise on cyber safety – we would love for you to get involved. As many of you know, cyber security is a shared responsibility. Here’s what you can do to help:
- Promote Cyber Month on your own personal social media channels
- Follow cyber security best practices at work and at home
- Talk about cyber security with friends and family – here are resources to help you (simply select the topics that mean most to you)
Thanks in advance for your help in keeping Canadians safe online. We wish you a very safe and happy Cyber Month!
Week 4 - Starting new habits
A secure future starts when you form strong cyber safe habits!
Start today by learning to spot suspicious messages and files that could lead to malware or ransomware.
Ransomware 101: How to stay cyber secure
Most of us have a seen a hostage movie before. It is, after all, a pretty common Hollywood formula: Bad guys storm a bank (or high-rise in Los Angeles or shipping boat), take a bunch of hostages, and then make demands before they release them.
Now imagine that scenario, except:
- The bad guys = Cyber criminals
- Hostages = Your computer, devices and any files that may be on them
- Demands = Requests for money
That’s how ransomware works.
Don’t worry, though – you don’t need to be a superhero to stay secure.
Here are the steps you can take to ensure you aren’t a victim of a cyber criminal’s attack.
 What is ransomware
What is ransomware
Ransomware is a form of malware that infects your computer or device. When ransomware takes control of your computer or device, it locks you out of that computer or device entirely or certain files.
To get the ransomware on your computer or devices, cyber criminals trick you into downloading a program that looks legitimate. But what you’re really downloading is a piece of software designed to take control of your information so you can no longer access it.
They then refuse access to your computer, devices, or files unless you pay a ransom.
You’ll usually know when you have ransomware if you receive a notification stating that your computer or data has been locked and a demand that a payment be made for you to regain access. Sometimes the notification states that authorities have detected illegal activity on your computer, and the payment is a fine to avoid prosecution.
There are two common types of ransomware:
- Lockscreen ransomware: displays an image that prevents you from accessing your computer
- Encryption ransomware: encrypts files on your system's hard drive and sometimes on shared network drives, USB drives, external hard drives, and even some cloud storage drives, preventing you from opening them
How to protect yourself from ransomware
No strategy for cyber security is completely foolproof. But, like with putting winter tires on your car during the colder months, there are steps you can take to lessen the risk.
Here are steps you can take to protect yourself from ransomware attacks:
Avoid suspicious downloads
The best way to protect yourself from malware generally is also the best tactic for protecting yourself from ransomware: Avoiding suspicious downloads.
The most common tactic cyber criminals use for spreading ransomware is deception. They trick victims into downloading a piece of software that looks legitimate but is in fact ransomware.
Cyber criminals commonly spread ransomware through email attachments, infected programs, and compromised websites.
Regularly back up your files
Regularly backing up your files is a key defence against ransomware. It means that, if you do become a victim of a ransomware attack, you have an easy “out”. Ideally, you would have a back up somewhere other than on your device, such as on an external hard drive or on the cloud, so you can recover your files if your device is locked.
Backing up your files takes some of the sting out of a ransomware attack. After all, if you have a back-up, cyber criminals won’t be able to hold your information ransom.
Keep your operating system updated
Updating your operating systems offers a lot of benefits for protecting your devices from cyber attacks. This includes ransomware.
By updating your operating system whenever updates become available – rather than continually putting them off – you can reduce the chances of your devices getting infected.
What to do if you get infected with ransomware
Hopefully, you’ll never be a victim of ransomware. But the fact is that cyber criminals are skilled at tricking their victims into downloading files or clicking on links that look legitimate.
Despite what you may do to protect yourself, you still could become a victim.
If you do become a victim of a ransomware attack, here’s what you should do:
- Do not pay the ransom. These threats are meant to scare and intimidate you, and they do not come from a law enforcement agency. Even if you submit payment, there is no guarantee that you will regain access to your system.
- Disconnect your device from the internet so that you can prevent the ransomware from spreading to other connected devices.
- Contact a reputable computer technician or specialist to find out whether your computer can be repaired and your data retrieved. However, if you had saved a backup to the cloud or on a hard drive you will be able to easily recover your files.
- Contact the Canadian Anti-Fraud Centre to report the incident and contact the Canadian Centre for Cyber Security to report the ransomware.
Conclusion
The prospect of getting a device infected with ransomware is scary. But by taking the right steps you can significantly reduce the chances you will be a victim of a ransomware attack.
Week 3 – Cyber threats are evolving – are you?
As cyber threats like phishing evolve, it's important to keep your knowledge up to date.
What is phishing?
Phishing happens when cybercriminals send mass messages pretending to be from a legitimate source, like an individual or organization you may know (including government agencies), to try and steal your personal information. Phishing attempts are often delivered using emails, phone calls, text messages and direct messages on social media.
Smishing, phishing attempts through SMS (text) messages, is a common form of phishing. Cyber criminals send text messages that typically include a link that they’re trying to get you to click on. The messages are often disguised to look like a legitimate contact and website, but the message contains a spoofed (fake) link designed to trick you into clicking on it. The links can contain malware (malicious software) to infect your device or bring you to spoofed websites to input your personal information. But smishing attempts don’t always include links. Cyber criminals may also try to get you to reply with information they’re looking for, like your social insurance number or account information.
Transcript - SPAM 7726
Reporting suspicious text messages to 7726
The best protection against smishing attempts is to be cautious about any messages that you receive from phone numbers you don’t recognize or that seem like a suspicious request. If you’re in doubt about the legitimacy of a sender or message, contact the legitimate source using another medium. Most importantly, don’t reply and never click on any links.
Instead, forward the spam message to 7726 (SPAM on most keypads). This will alert your cellular provider to open an investigation on the contents of the message. Canadian telecommunications companies take spam messages very seriously. Reporting to 7726 allows them to identify new types of smishing and block spam messages for all users. Forwarding methods will vary depending on your phone.
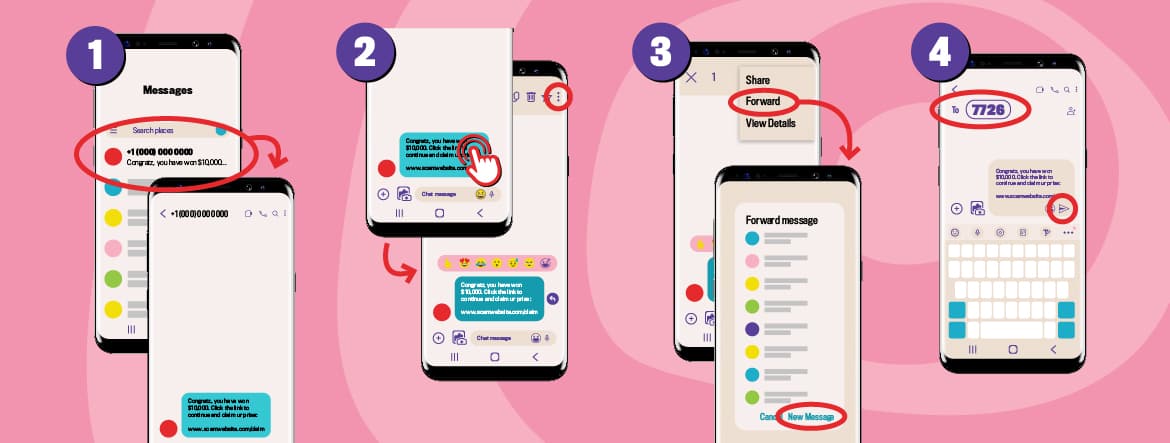
Long description - How to forward a phishing message on Android device
To forward a phishing message on an Android device:
- Tap the message (ensuring not to click on any links within the message) to open the conversation view
- From the conversation view, press and hold the message you want to forward until a menu prompt appears
- From the menu prompt select Forward (or an arrow icon), which directs you to a new message draft or a contact list
- Enter 7726 in the To: field and press the send button.

Long description - How to forward a phishing message on iOS device
To forward a phishing message from iOS:
- Tap the message (ensuring not to click on any links within the message) to open the conversation view
- From the conversation view, press and hold the message you want to forward until a menu prompt appears
- From the menu prompt, select More… to present a checklist for messages to select for forwarding
- Select any additional messages to include and then tap the arrow icon (on the bottom right corner) to create a new message draft
- Enter 7726 in the To: field and press the send button.
In Canada, reporting spam to 7726 is free and will not count towards your data or messaging usage package. You can contact your cellular provider directly if you have questions about the reporting process.
Conclusion
Learning to spot the signs of a phishing is a great way to protect yourself and always be cautious of unexpected or suspicious messages. A legitimate organization, including a Government of Canada department, will never try to conduct business over a text message.
Recognize artificial intelligence (AI): 9 ways to spot AI content online
Images, videos and text created by artificial intelligence (AI) can be found just about anywhere online — but if they’re not labeled, you may not even realize it. This can spread disinformation which is false information that is deliberately intended to mislead.
Learning how to identify AI generated content is key in making sure you’re not misled. Here are some tips to help you out.
Images
Watch out for misplaced content
When it comes to spotting AI, the details really do matter.
Look out for:
- Missing or misplaced objects or body parts (especially hands)
- Incorrect shadows and lighting
- Text that doesn’t make sense or form real letters
Be suspicious of smooth features
AI often creates unrealistic textures for skin and fabric.
Look out for:
- Humans who appear glossy or have unusual smooth skin or clothing
- Smooth, crisp images with heavily blurred backgrounds
Check for watermarks
Some AI apps add a watermark, like a small logo, to the images they generate.
Look out for:
- Icons or text on an image indicating it was created with AI
Videos
Be aware of body language
AI doesn’t always create natural movements when making humans or other creatures move.
Look out for:
- people who don't blink
Consider lighting
Consistent lighting isn’t always common in AI-generated videos.
Look out for:
- shadows, blurs or light flickers where there shouldn’t be
Listen for irregular audio
Audio, especially voices, can be a sign of AI generation.
Look out for:
- Unnatural and flat tone
- Unexpected background noises
- Choppy sentences
Text
No emotion
Unlike human writing, AI-generated content is often uniform and factual.
Look out for:
- Writing that doesn’t include personal opinions
- A dry, “robotic” or matter-of-fact tone
- Emotionless formal writing
Do a fact-check
Some AI tools are trained on old data, giving false information about current events.
Look out for:
- Information that’s out dated
- Exaggerated “facts”
- Fake sources and references
Watch for repetition
Even AI has favourite words and phrases.
Look out for:
- Words or phrases repeated over and over again
Don’t fall for online AI-generated content
- Check your sources to see where information is from
- Reverse-search images to find their original context
- Don’t rely on AI detection tools as they are often unreliable
Week 1-2: Preparing your future self today and bringing your devices up to speed
Getting ready for the future starts with you – which is why we’re kicking Cyber Month off by helping you secure your accounts. This week, we’ll cover relatable and unexpected ways account security can help you today and in the future by discussing:
- password managers
- multi-factor authentication (MFA)
- social media accounts
- private networks
- storage and backup
A solution to password overload
A strong password is an essential part of keeping your information safe. Unfortunately, it’s often the case that the more complex a password is, the harder it is to remember — especially if you’re using different passwords for every account.
You can easily keep track of all your passwords by using a password manager: a password vault that stores all your usernames and passwords for different websites, apps and devices.
Make your password manager work for you

Choose the right password manager
Not all password managers are equal. Make sure the password manager you choose has security features like:
- multi-factor authentication
- prompts to change old passwords
- notifications about weak or reused passwords
- integration with your other devices
Password managers can be part of your favorite browsers, a standalone application you download , or can be part of your device operating system .

Keep your primary password safe
The password to your password manager is the key to every account you have, so you need to be extra careful keeping it safe.

Enable multi-factor authentication
Protecting your passwords with just another password isn’t enough. Enable your password manager’s multi-factor authentication to create a secure system only you can access. Learn more about multi-factor authentication.

Remember your most sensitive passwords
Password managers are a useful tool, but they may not be the best choice for all passwords. Passwords for sensitive accounts like your email and bank should be stored the old-fashioned way: in your head. Learn more about creating a strong password.
Practice safe social
Social media sites like Facebook, Twitter and Instagram are a great way to stay in touch with family, connect with friends, share news and post photos.
But if you’re not careful with how you use it, social media is also an easy way for cyber criminals to learn more about you. Make sure you take precautions before you post.
Protect your profile

Use a passphrase or complex password
Social media is all about sharing, so if your password is something you’ve shared on social media, like your pet’s name, it will be easy for a cyber criminal to guess. Make sure you use a unique passphrase or password for every social media account. Learn more about creating a strong password.

Enable multi-factor authentication
Most social media sites offer multi-factor authentication (MFA). Always turn MFA on in your settings to keep your account secure. Learn more about multi-factor authentication.


Keep private information private
Even if you’re careful, you can never know who’s on the other side of the screen. When you post on social media, avoid sharing:
- Personal information like your phone number, email address, home address, work details or your child's school
- Informative pictures: Check the background of pictures before you post for any revealing info like street signs or license plates.
- Geotagged photos: Most smartphones and digital cameras automatically attach the exact location where a photo was taken. Many social media sites don’t capture this information when you post a photo. But when they do, turn off geotagging in your camera’s settings and remove geotags from older photos with photo editing software.
- Exciting news: Vacation details, big purchases or events with your address can let criminals know there’s an opportunity to rob your home while you’re away.
- Banking or financial information, including the name of your bank, credit or debit card numbers, and any other financial information.
Keep your Wi-Fi to yourself
Your Wi-Fi network is the gateway to all your connected devices. Making sure your Wi-Fi is secure doesn’t just prevent other people from using your internet, but it also helps keep your devices and your data safe from potential intruders.
Your computers, phones and maybe even your lightbulbs share a Wi-Fi network; it’s important to make sure your network is as secure as possible.
Use your private network safely

Use a passphrase, or a strong password
We recommend that you use passphrases, as they are longer yet easier to remember than a password of random, mixed characters. A passphrase is a memorized phrase consisting of mixed words with or without spaces. For example: LampFloorPlantDoor.
If your router requires a traditional password, make sure it’s strong. A strong password should include:
- At least eight characters
- A combination of upper- and lower-case letters and at least one number
- At least one character that isn't a letter or number, like !, # or $.

Limit area coverage
Try to keep your coverage area limited to your house by placing your router as close to the middle of your space as possible, rather than placing it near windows.

Update your devices
Make sure that every device on your network, including routers, computers, smartphones, and smart devices, have updated software and operating systems to keep your entire network protected.
Protect the files that matter most
We store our most important, often irreplaceable, files on our computers and phones. Duplicating and securely storing those files prevents us from losing them.
Backing up your data keeps it protected in any number of unforeseen circumstances, from accidentally erasing files to a total system failure in which your files and documents are destroyed.
Secure your important data

Keep your files organized
Organize files and documents using folders and sub-folders instead of leaving them scattered around your desktop.
Back up what matters
Back up any files you want to protect, like family photos or financial documents. You don’t need to back up applications, utilities, or your operating system (OS) — those can be reinstalled later.

Choose the back up solution that’s right for you
There are different options you can use to back up your files.
Cloud storage saves your files, documents and photos to a remote database. A cloud storage service may come standard with the operating system (OS) of your computer or device. Find out if your device does automatic backups to a cloud by searching for it in your OS’ system preferences or settings menu.
External hard drives are devices that can be connected to your computer or device to save a copy of files, documents and photos. Connect your external hard drive regularly to back up files. Remember to disconnect it when the backup is complete.
External storage can also be done on a USB key, CDs or DVDs.
For extra peace of mind, consider backing up your files on two different storage devices. Remember, backing up your files and documents externally can help you recover them if they become damaged or compromised.


Protect your back-ups
Whether you’re using the cloud or a physical back-up, enable passwords or use other encryption security whenever possible.
You can also keep your data back-up storage separate from your computer, or even away from home, to minimize the chances of both being stolen or destroyed.

Know where your cloud is coming from
If you’re using cloud storage to back up your data, review the privacy policies and security features offered by your cloud provider. For example, providers may offer several months of historical file recovery or protection from ransomware . Make sure to use a strong password for your cloud service.


